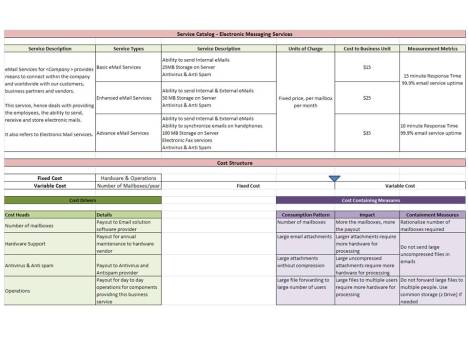
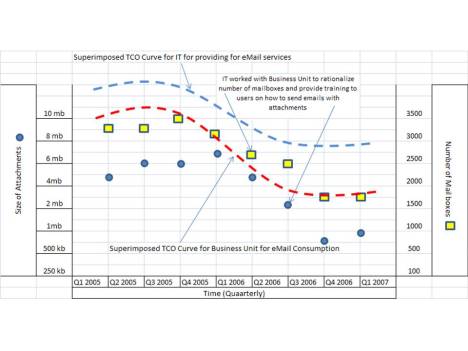
initially i had titled this post as “email and its imminent demise” but then maybe it is incorrect to say “imminent demise”, rather i think it will slowly move into the background and slowly treated as legacy application if it fails to evolve and incorporates the new web 2.0 technologies that ppl are toying for enterprise use..
email has come a long way since it was invented in early 1970’s. people have used emails to send simple messages to each other/group, use it as means of sharing documents (much to the plight of the email administrators), use calendaring features for appointments and scheduling meetings. on looking closely at how an email is typically used in an organization, i have noticed that along with the above mentioned functions, emails are also used as means to store files (hey dude, can u email me that presentation that you took for a xxx client the other day, i may use it in future), approvals for certain business transactions (e.g approval to buy a new server sent by CIO to IT Manager etc), keep a record of certain communication (he said, i said etc) to basically CYA (covery your a**) in case things go bad..however, along with email came its nuances, maintaining uptodate address book, spam, compliance issues etc. but we are all dealing/living with it.
as time goes by, in the world outside the boundaries of an enterprise, people are adopting techniques that harness the power of technology to reach out to each other, either as part of social networking phenomenon or to work together/collaborate. with the power of the internet coming to the mobile device, the speed at which this adoption is taking place is awesome. now, people dont need to access their emails to know what their friends/peers are doing or what is the latest buzz etc. applications like facebook and twitter have already proven the usefulness of technology outside the enterprise walls..it is only a matter of time when they are adopted within the enterprise also. already there is a lot of talk about web 2.0 adoption within the enterprise by many analysts. email too needs to evolve if it has to stay alive in this fast changing scenario. already there are surveys which shows that more and more people are using facebook/myspace/twitter etc over email to reach out/keep in touch.
in my opinion, organizations will start looking for a better collaboration platform which can increase the effectiveness, efficiency & productivity by harnessing the same technologies that are used by millions outside the enterprise boundaries. realizing this need, some email services have now integrated instant messaging/chat services with archiving features on the messaging platform. . how many times have you noticed that when ur having an email exchange with someone, u end up taking the remaining conversation to the chat as it is faster and more effective. i think the collaboration tools like instant messaging will evolve and bring convergence of channels of communications viz chat, voice, video along with email and other forms of collaboration technologies like document management systems etc. the other day i wanted to reach out to a group within my company to work on platform migration. instead of sending emails to numerous people and then getting redirected from one group to another, i just sent an update on yammer and got a reply within 2 hours from someone located on the other side of the world.. it was awesome and saved me numerous emails and days in waiting for a favorable response.
there will be initial resistance from many to move from legacy to new forms of collaboration. there will be compliance & security concerns. but like the case with any new technology, it will find its own steady state adoption rate. only that, given the way web 2.0 is evolving, this rate might be accelerated by few notches.
already there is a lot of noise that google wave has generated on the internet. maybe microsoft solution around corporate instant messaging – OCS will also evolve to bring in convergence of existing communication & collaboration tools with the new web 2.0 toys.
my take is that few years from now, email might just end up as a legacy platform required to retrieve old email data and corporates will use a newer and more efficient form of collaboration technologies.
Filed under: IT, IT Infrastructure & Operations, IT Models for Enterprise, IT Strategy, SeamlessIT | Tagged: Business-IT Alignment, End User Computing, Infrastructure Outsourcing, IT Infrastructure & Operations, IT Models for Enterprise, Making IT Simplified | Leave a comment »